
The Complete Office 365 and Microsoft 365 Licensing Comparison
Understanding Office 365 and Microsoft 365 licensing can be difficult. In order to best pick the solution for your business, we found a table for your reference.
Helix Systems is proud to be the Official Acronis delivery partner of HMD Motorsports (INDY NXT) Learn More

Understanding Office 365 and Microsoft 365 licensing can be difficult. In order to best pick the solution for your business, we found a table for your reference.

It’s finally time to say goodbye to Flash. Adobe will no longer be supporting Flash Player after December 31, 2020 and Adobe will block Flash content from running in Flash Player beginning January 12, 2021. We have 2 steps to remove Flash Player the one that comes with Windows 10 and one that you can install yourself.

Often in business and personal life, people make decisions that make sense in the short-term, but the long-term, the ramifications of those choices become apparent. This fact is especially true when it comes to businesses making purchasing decisions for technology.

As virtual gatherings become more commonplace, here are some tips and considerations for using Zoom for hosting these virtual events.

Security as a service (SECaaS) is a service where a third-party manages the cybersecurity needs of your company. SECaaS also provides subscription-based services similar to those offered by Software as a Service.
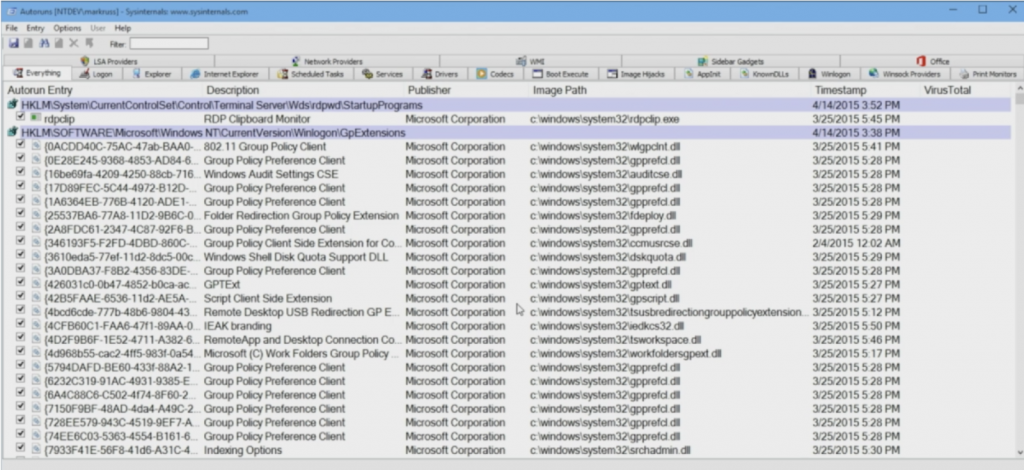
The Sysinternals utilities are vital tools for any computer professional doing any sort of deep Windows OS troubleshooting

What our thoughts are on password protected documents, how to unlock them, and how to secure your passwords moving forward.

There is so much outdated, misleading, and just plain wrong information about passwords. We want put to rest some of the most persistent falsehoods about passwords and talk about what it takes to come up with strong passwords and practice good password security in 2020.

Is your company switching from in-person to virtual meetings? All insight you need on how to hold productive remote conferences.

Over the years, technology has become an integral part of running a business. Overall, businesses have benefitted greatly due to automating tasks that would require hours of manual labor. However, not understanding how to use and manage technology have cost businesses many hours of payroll.
We’re happy to answer any questions you may have and help you determine which of our services best fit your needs.
We schedule a call at your convenience
We conduct a discovery call
We prepare a proposal
We guarantee a 15% reduction in your IT spend — or we’ll cover your next month’s bill.
Book a free audit and see exactly where your firm can save.